The microblogging site Twitter is adding the option to use security keys as the sole 2FA method — meaning you can enroll one or more security keys as the only form of 2FA on your Twitter account without a backup 2FA method.
Starting today, people on Twitter have the option to use security keys as their only form of two-factor authentication (2FA).
Now security keys can be your one and only two-factor authentication method on mobile and web.
— Twitter Support (@TwitterSupport) June 30, 2021
Learn more about how security keys can protect your account from attacks: https://t.co/Ta7uQSFhi6 pic.twitter.com/aPDOnbRtVk
While any form of 2FA is better than no 2FA, physical security keys are the most effective. Security keys are small devices that act like keys to your house. Just as you need a physical key to unlock the door to your home, you need a security key to unlock access to your account. Security keys offer the strongest protection for your Twitter account because they have built-in protections to ensure that even if a key is used on a phishing site, the information shared can’t be used to access your account. They use the FIDO and WebAuthn security standards to transfer the burden of protecting against phishing attempts from a human to a hardware device. Security keys can differentiate legitimate sites from malicious ones and block phishing attempts that SMS or verification codes would not.
@AndySayler and @abbasalih wrote in a blog post.
Twitter has long encouraged the use of some form of 2FA. In 2018, the company added the option to use security keys as one of several 2FA options. However, this initial support only worked for Twitter.com, not the mobile app, and required accounts to have another form of 2FA enabled as well.
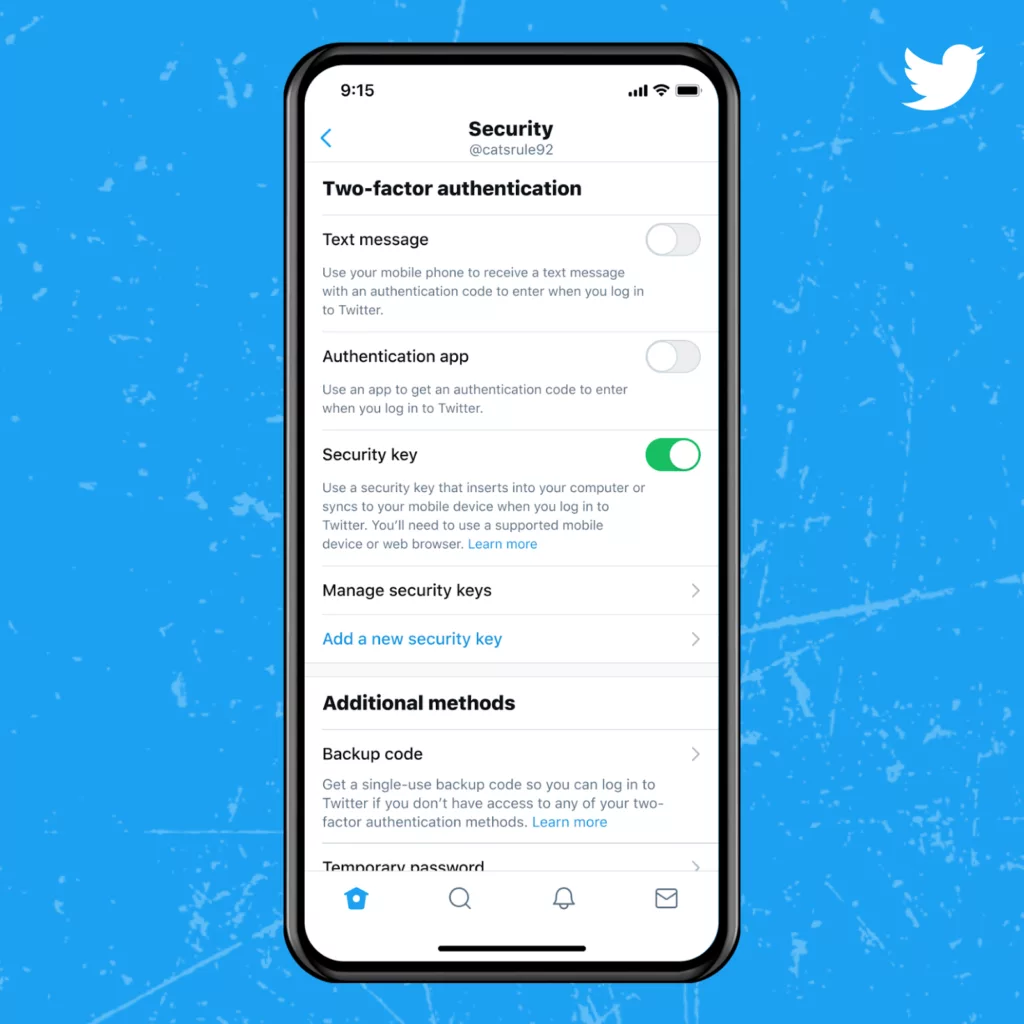
In recent years, Twitter has added a number of features to beef up login security. The company expanded beyond SMS in 2017 by adding support for authentication apps like Google Authenticator and Authy.
Bijay Pokharel
Related posts
Recent Posts
Subscribe

Cybersecurity Newsletter
You have Successfully Subscribed!
Sign up for cybersecurity newsletter and get latest news updates delivered straight to your inbox. You are also consenting to our Privacy Policy and Terms of Use.




